Three Surprising Ways Your Smartphone Can Be Used to Spy On You
Everybody knows that carrying a smartphone in your pocket is like keeping a personal tracker on you at all times. We sacrifice a lot for convenience.
In exchange for quick searching, we hand over a great amount to Google. To keep in touch with family and friends, we give Facebook so much information about ourselves. And there were concerns over how Pokémon Go could infringe on your privacy.
But you might not know that your photos, Bluetooth, and even smartphone battery could be used to spy on you ...
Geotagging Data Stored On Your Photos
Exchangeable Image File (EXIF) information is incredibly handy, whether you're a professional photographer or an amateur. This data is included whenever you take a picture using your smartphone or digital camera; for the latter, that EXIF information can include date and time the photo was taken, focal length, camera used, and orientation. If you're impressed with the exposure, checking out the EXIF data can help you recreate it.
Smartphones, too, include the date stamp of when images were taken; scroll through an iPhone and each picture will include that identification. If you saved an image from online, you might find either the date you added it to your Photo Stream or when it was actually taken by its original owner.
Due to smartphones' geotagging capabilities, however, the information stored includes your location.
As long as you use GPS, you can successfully trace where you've been. Combining this data with what's included in photos, a stranger could work out where you go on holiday, which events you regularly attend, and yes, where you live.
In most cases, that's not too much of a worry. After all, you're the only one flicking through your phone, right? Putting aside possible theft, issues could arise if you're passing your device on. Even factory resets do not completely wipe all phones - that's why you should always encrypt your data before selling or recycling any hardware.
Another concern is hacking. I'm sure you remember when the iCloud accounts of numerous celebrities were hacked into and NSFW images were leaked. That's a fine example of cybercriminals obtaining not only potential blackmail material, but also a worrisome amount of metadata. Similarly, social media accounts have been hacked, including Snapchat. Fortunately, Facebook and Twitter automatically remove embedded information, so you do not need to trouble yourself further there.
What can you do? Most smartphones give you the option of removing geotagged metadata, and it's surprisingly easy.
On an iPhone, for instance, you simply click on Settings> Privacy> Location Services, and near the top of the list of apps that do want use of your GPS, you'll find Camera. If it's on While Using the App, change it to Never. While you're there, you might as well check you're happy with the apps that do currently have access to your location.
On Android, open the camera app, tap on the menu, then the gear icon to see settings; from here, you should see something like Location, GPS tag, or Geotag, depending on the device, and disable it.
Is Bluetooth Compromising Your Location and Contacts?
While most of us are used to sending information between cell phones over Wi-Fi, we had to rely on Bluetooth for ages. It's a wireless short-range connection between devices, still found in smartphones because it's very useful, particularly if you're trying to use speakers, a hands-free kit, or, if you're not put off by our cautionary article, a keyboard.
The latest Bluetooth has potential, but many still hate it. And a big part of that is how "discoverable" you are.
If you've not toggled your settings accordingly, others can easily find your device using Bluetooth. That sort of surveillance is troublesome, and could be used by shops, for instance, to specifically target you. Shop surveillance is even capable of noting how often you visit a certain section of the store. Stores already use Wi-Fi analytics to trace customers, but Bluetooth is a good alternative.
Nonetheless, there's a myth that changing your Bluetooth to "non-discoverable" protects you. Sadly, hackers are smarter than that.
This has led to Bluejacking - that is, sending malicious content to your phone via Bluetooth, including eavesdropping software, and malware. In 2012, for instance, the security suite firm, Kaspersky Labs uncovered Flame, malware used in places like Israel, Sudan, and Syria but most widely found in Iran. Due to its considerable file size (and the fact it took at least two years to be discovered), Kaspersky claimed it was:
"[O] ne of the most complex threats ever discovered."
It used Bluetooth to search and download contact names and phone numbers from not only the user's device but also any nearby Bluetooth-enabled smartphones. Furthermore, after installation, the malware could record calls, including Skype, and take screenshots, including in-private messaging and emails, then send material back to its originator. Needless to say, it was a fantastic toolkit in a secret services' arsenal.
That shows Bluetooth's potential for spying on you.
What can you do? Being aware of the problem is a good first step, especially if you naïvely think iPhones do not use Bluetooth. (I'm not criticizing: I was unaware of that for some years too!)
One line of defence, of course, is a solid four-digit passcode. Do not go for something obvious. Your best bet, though, is turning Bluetooth off, preventing hackers from getting into your device. "Non-discoverable" might seem like a safe option, but it's much better if you simply turn Bluetooth on solely when you intend to use it.
Yes, Your Battery Can Spy On You
This sounds utterly bizarre, but it's come to light, relatively recently, that your smartphone battery can be used against you.
It started with good intentions: websites and apps can request information automatically from your smartphone about how much battery you've got left; if it's low, the site can then present a lower-power version of itself so it does not burn up your much-needed charge.
But research, collated from a study of the top 1 million sites, suggests that some services can use that data to spy on your online activities and bypass privacy measures you might be employing already, like using a Virtual Private Network (VPN). It's a scary thought because there's very little you can do about it.
The immediate concern was that the protocol can be carried out without the user's permission, but that did not set off too many alarms as it was solely to send data on the estimated time until the battery dies, and how long it'll take to charge. But combined, these can form an identifier, especially as the information reloads every 30 seconds. That means that two seemingly-separate data sets (through private browsing or the aforementioned VPN) can be linked, so no matter how you try to evade detection, your browsing can be tracked.
Visiting the same site frequently means your cookies can be reinstated, even if you've cleared them, a practice known as respawning; doing it for an extended period - those sites you visit every morning before your start work, for example - can result in a more definite unique identifier being assigned to your device.
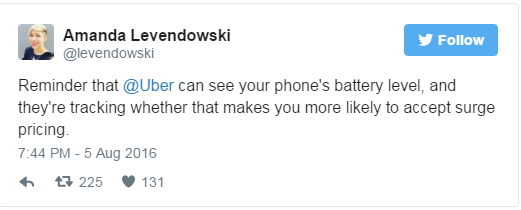
This might not seem too troubling (after all, we're used to being tracked online by all sorts of services, including those Facebook sharing buttons), but there are real-world consequences. A notable one is Uber, the popular taxi company, which denies any questionable business techniques but admits potential is there to charge its customers more when their battery's nearly dead. Uber's head of economic research, Keith Chen says:
"When your phone is down to 5% battery and that little icon on the iPhone turns red, people start saying," I'd better get home or I do not know how I'm going to get home otherwise. "We absolutely do not use that to push you a higher surge price. But it is an interesting psychological fact of human behaviour. "
What can you do? This is a difficult practice to battle against. Data is collected if your battery's low, so keeping it topped up is a good move, as is avoiding apps that sap it. Otherwise, you might want to consider only visiting sites you go on regularly on one specific device (maybe your work's PC) so your smartphone is not tracked relentlessly.
Smart Spying?
Subterfuge is the ideal method for tracking, at least to those who want as much of your private information as they can, so spreading the word certainly helps. Nonetheless, surveillance will always evolve, and these three examples highlight how smart services can be.
Which other tracking methods surprise you? How do you fight against Big Brother?
Three Surprising Ways Your Smartphone Can Be Used to Spy On You
 Reviewed by BTG
on
6:09:00 AM
Rating:
Reviewed by BTG
on
6:09:00 AM
Rating:
 Reviewed by BTG
on
6:09:00 AM
Rating:
Reviewed by BTG
on
6:09:00 AM
Rating:
















Post a Comment